| Table of Contents |
|---|
Datameer X Implementation
Datameer X allows administrators to leverage their underlying security setup by running in secure cluster mode with secure impersonation enabled. Enabling impersonation, along with configuring Datameer X to use a remote authenticator with access to the HDFS user community, allows Datameer X to access HDFS as the user logged into Datameer X and to run Hadoop jobs as the owner of the artifact and to preview data. This ensures that the underlying HDFS permission setup is respected by Datameer :X
- Data accessed via an HDFS connections is subject to HDFS permission checks by the user running any Datameer X job.
- Datameer X permissions set on import jobs, data links and workbooks are workbooks are pushed down the HDFS layer for all imported data, job result data, and job artifacts.
- Export jobs to a secure HDFS connection also respect the permissions set on the export job.
The Datameer X process is run by a member of the HDFS supergroup and is configured to proxy other users when submitting jobs or accessing HDFS. Datameer X achieves this by using the secure impersonation feature, behaving similarly to the workflow manager, Oozie. For more information see secure impersonation.
...
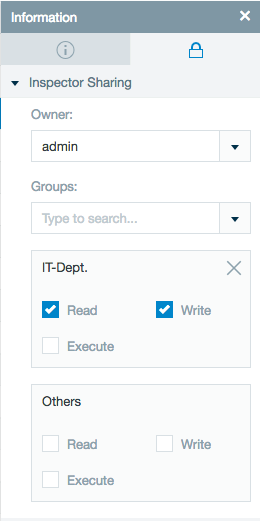
One key difference in behavior with secure impersonation enabled is the Datameer X entity permission system changes to single group mode. What this means is that everywhere in the system where you specify entity permissions instead of having the options to configure permissions for a set of groups you are forced to provide permissions for exactly one group in addition to "Others". This is because job artifacts are stored in HDFS using these same permissions and HDFS permissions follow the POSIX model of owner, group and all permissions.
As an example, with the following import job permission setup in Datameer :X
The HDFS data associated with running this job are as follows:
...
| Warning | ||
|---|---|---|
| ||
Groups need to be in both Datameer X and in HDFS to be properly configured. |
Cloudera Sentry and Hortonworks Ranger integration
When Sentry or Ranger are on a Hadoop cluster that has the impersonation plug-in enabled, Datameer X acts as a DFS client and respects the (Sentry or Ranger) permissions.
The Datameer X private folder in HDFS should be owned by datameer:<dasuser>, which is the group that is specified for impersonation, including its core directories. To ensure this ownership, run secure_hdfs_tool.sh.
If you want Datameer X users to access resources that are controlled by Sentry or Ranger, then proper privileges and user mapping need to be set from that software.
...