| Warning |
|---|
After upgrading from a version prior to Datameer X 6.3: If authenticating with Active Directory or LDAP, users executing jobs must be listed in the authenticator. For added security, executing jobs as a users not present in the authenticator is no longer possible. |
Overview
The LDAP and Active Directory authenticators available in Datameer X provide remote authentication services for Datameer X users. Administrators can configure Datameer X to use their existing LDAP or Active Directory systems as the authenticator of record allowing for centralized management of user accounts and credentials outside of Datameer. Users can authenticate with Datameer X using existing credentials which are verified against the remote system on every login. If the remote system no longer sanctions the user, access to Datameer X is denied. This simplifies Datameer X administration and allows end-users to use familiar single sign-on credentials when accessing Datameer.
| Table of Contents |
|---|
Users and Groups
When using the LDAP Authenticator, credentials are authenticated at the time of login directly against the remote service. In order for Datameer X to manage authorization and object permissions, a Datameer X user entity is required to represent the remote user. It useful to think of users being imported into Datameer X from LDAP with the remote server always ensuring that users have valid, active credentials. For details on how to add users from LDAP, see Importing Users. When a user is imported into Datameer X a user entity is created using the remote unique identifier as the Datameer X username and populated with other account details, i.e email address.
During import, Datameer X creates groups based on the groups contained in the LDAP directory. This allows the use of existing LDAP groups for Datameer X access control as the group memberships are mirrored across systems. The users' group memberships and user details are updated on every login to ensure that any changes to authorization policies in LDAP are reflected in every Datameer X session. Since we rely on LDAP groups when the LDAP Authenticator is in use, there is no facility to create groups within Datameer*. Datameer X can handle at maximum 500 LDAP groups.
* See Using a Default LDAP Group for the one exception to this rule.
| Note | ||||
|---|---|---|---|---|
| ||||
Many times an all lowercase username is required for proper Unix group authentication. Instead of needing to change all user names to lowercase characters, Datameer X has the following property file to transform a username into all lowercase before passing it to the hadoop client API(s) to account for this issue.
To enable this feature, add the above property file to the custom Hadoop properties. |
Configuration
| Note | |||||
|---|---|---|---|---|---|
| |||||
We strongly suggest that you have superuser mode enabled and that you have the password handy when making changes to the Datameer X authentication system. This helps to prevent being locked out of the system should something go wrong. Make sure the deployment property das.superuser.enabled is true and that you are aware of the values of das.superuser.username and das.superuser.password. You need to set the following in
|
| Tip | ||
|---|---|---|
| ||
If you plan on accessing your LDAP service over SSL, read Configuring Secure LDAP (LDAPS) before continuing. |
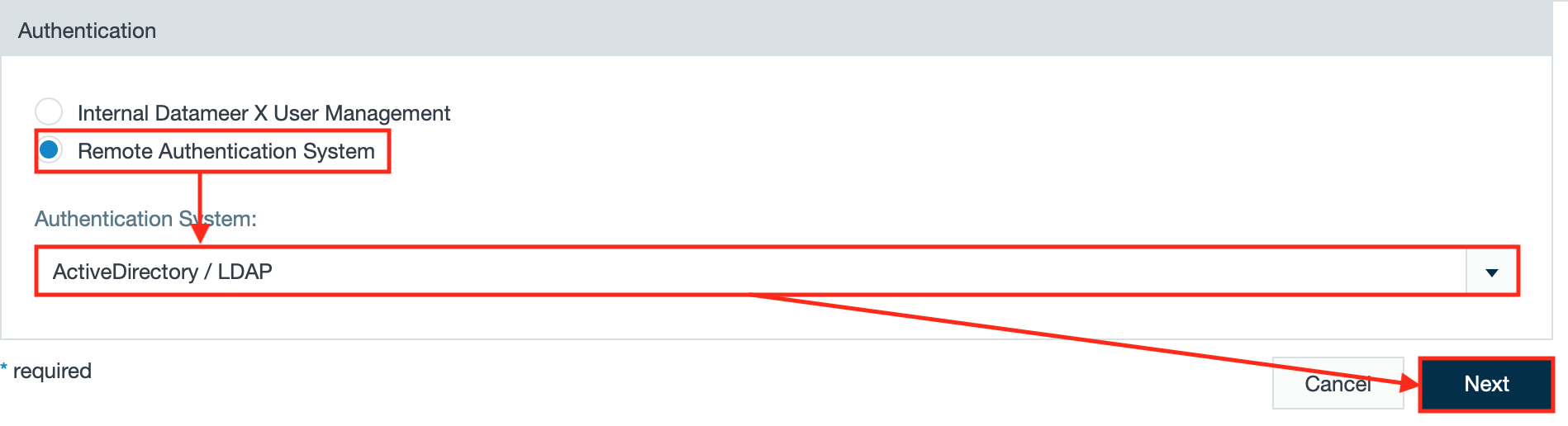
To configure Datameer X to use your LDAP or ActiveDirectory service, click the Admin tab, click Authentication on the left menu and click Edit. This presents you with the option to choose between the Internal Datameer X User Management or a Remote Authentication System. Select Remote and pick ActiveDirectory/LDAP from the drop down list:
Next, you see the configuration settings for you remote authentication service:
The configuration settings are described below:
...
Setting
...
Description
...
Server URL*
...
The LDAP connection string used to access your server. This should be in the form ldap://server:port. See Configuring Secure LDAP (LDAPS) for details on connecting via LDAPS.
Port numbers: LDAP/S - 389/636 or Active Directory - 3268
...
User
...
The user account Datameer X uses to connect to the remote service in order to perform authentication. For many LDAP services, this is a fully distinguished name of a user, for ActiveDirectory, this is username@domain.com
...
Password
...
The LDAP password for the user specified above
...
Search Base*
...
This is the LDAP location used as a search base. Datameer X bases its LDAP queries from here only searching below this point, so it is a good way to partition the users who are available to Datameer. You can only specify one search base. In Active Directory it is possible to limit Datameer X to users only contained in a specific domain or organizational unit using this setting. See Limiting LDAP User Results.
...
Pagination Control
...
Active Directory
Choosing the Active Directory service type configures the advanced query options with settings appropriate for most Active Directory installations. Also, a different strategy is used to list a user's groups which is required by Active Directory. If the default settings aren't appropriate for your installation they can be changed in the Query Options section. See Advanced Configuration.
| Warning |
|---|
Using Active Directory authentication for access to networked servers/services, like FTP/SFTP/SSH must ensure the primary group of the user doesn't contains a space. (E.g., The group "domain users" would fail. Change the primary group of the user to the single word "domain_users"). |
...
Advanced Configuration
To refine your authenticator configuration you can customize the settings Datameer X uses when communicating with the remote service. Expand the Query Options form:
...
Setting
...
Description
...
User Definition *
...
The filter expression used when Datameer X queries the remote system for available users. See Limiting LDAP User Results
...
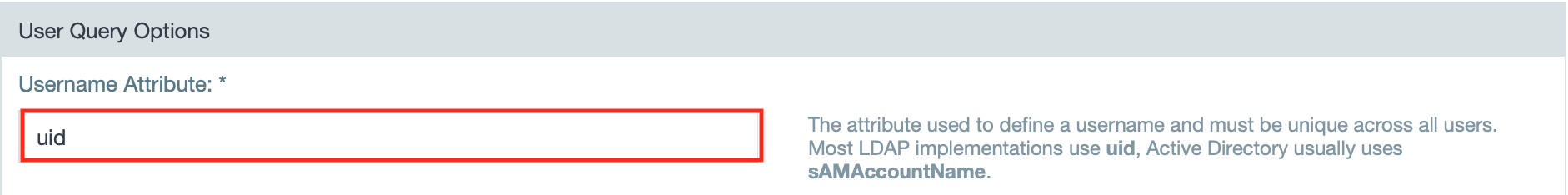
Username Attribute *
...
The attribute that is mapped to the Datameer X username. This must be unique across all users. For Active Directory this is the sAMAccountName, for other LDAP providers it varies: uid, cn, username, etc.
...
Email Attribute *
...
The attribute that is mapped to the Datameer X user's email address. Most systems use 'mail'.
...
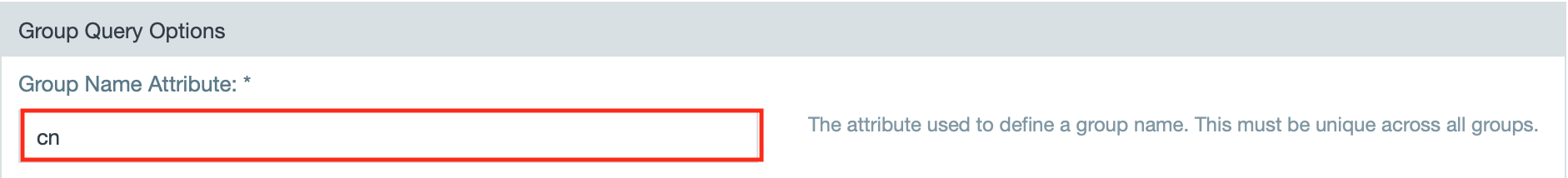
Group Name Attribute *
...
The attribute that is used as the group name in Datameer.
...
...
| Info |
|---|
Group Membership Attribute and Group Filter only apply to 'Other LDAP' installations as Active Directory installations use a different group listing strategy |
Configuration (As of Datameer X version 6.3)
| Info |
|---|
Datameer X has improved connecting and using authentication services.
|
...
The authentication configuration settings for Active Directory and LDAP are displayed.
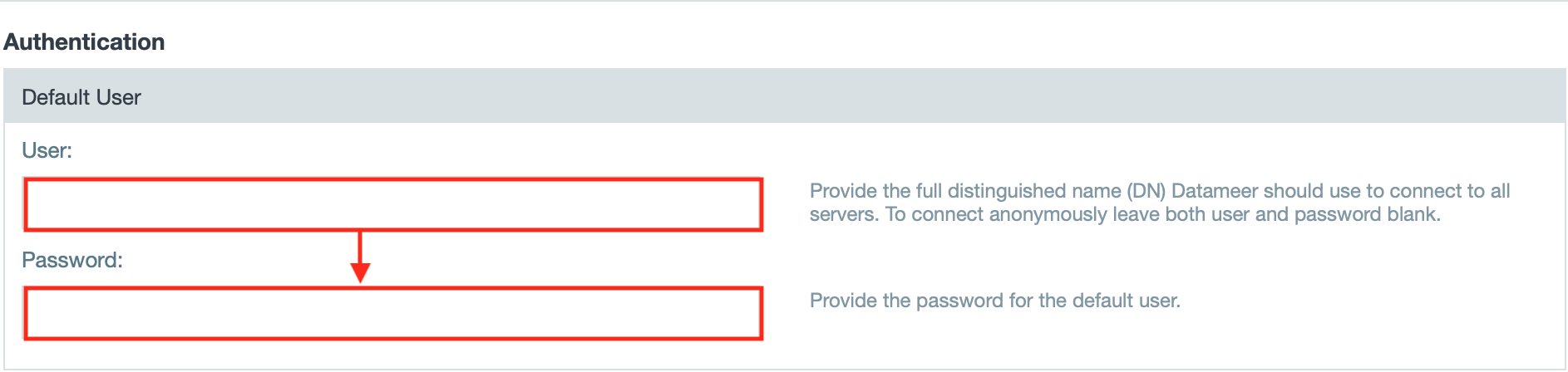
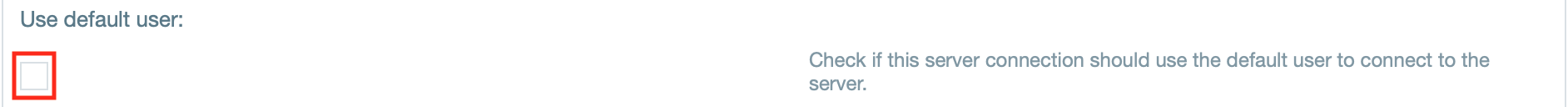
The default user values can be set when accessing multiple LDAP servers as the same user. If a default user/password is set, check the box under Server Connections that the default user values should be used to authenticate.
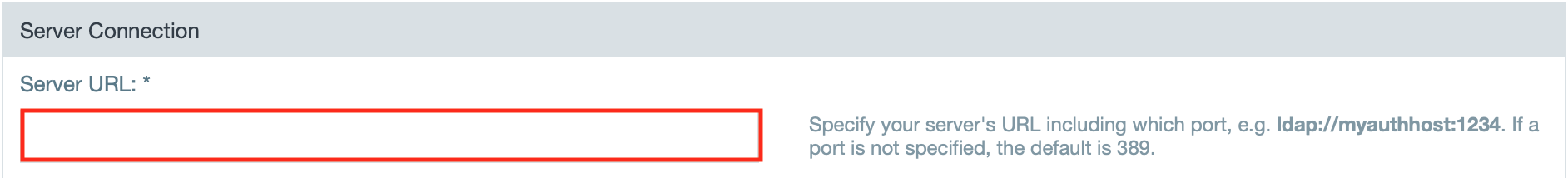
Enter the server configuration settings.
Multiple LDAP server can be added. Click the Add Server Connection button after all values have been entered. Datameer X validates the server and credentials and then provides a blank Server Connection settings form for additional servers.
...
Setting
...
Description
...
Server URL *
...
The LDAP connection string used to access your server. This should be in the form ldap://server:port. See Configuring Secure LDAP (LDAPS) for details on connecting via LDAPS.
Port numbers: LDAP/S - 389/636 or Active Directory - 3268
...
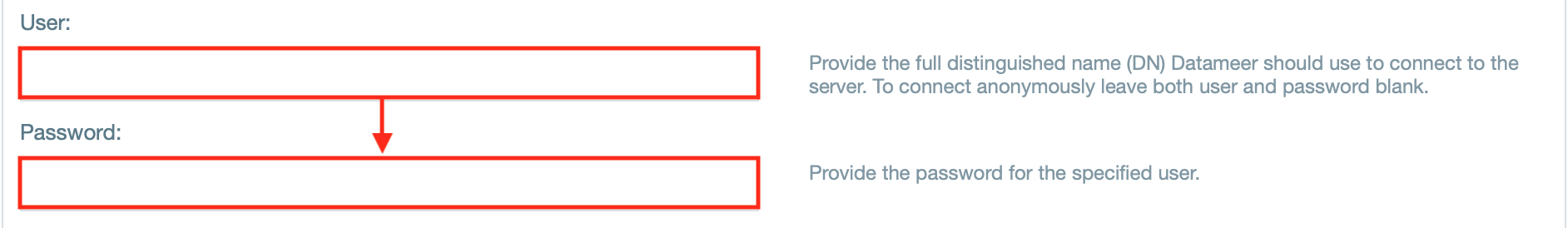
User
...
The user account Datameer X will use to connect to the remote service in order to perform authentication. For many LDAP services this will be a fully distinguished name of a user, for ActiveDirectory, this is username@domain.com
...
Password
...
The LDAP password for the user specified above
...
Search Base*
...
This is the LDAP location used as a search base. Datameer X bases its LDAP queries from here only searching below this point, so it is a good way to partition the users who are available to Datameer. You can only specify one search base. In Active Directory it is possible to limit Datameer X to users only contained in a specific domain or organizational unit using this setting. See Limiting LDAP User Results.
...
Pagination Control
...
User and group query options.
...
Email Attribute *
...
The attribute that is mapped to the Datameer X user's email address. Most systems use 'mail'.
...
The attribute that will be used as the group name in Datameer.
...
Group filters.
...
| Info | ||
|---|---|---|
| ||
The LDAP and Active Directory authenticators available in Datameer X provide remote authentication services for Datameer X users. Administrators can configure Datameer X to use their existing LDAP or Active Directory systems as the authenticator of record allowing for centralized management of user accounts and credentials outside of Datameer X. Users can authenticate with Datameer X using existing credentials which are verified against the remote system on every login. If the remote system no longer sanctions the user, access to Datameer X is denied. This simplifies Datameer X administration and allows end-users to use familiar single sign-on credentials when accessing Datameer. |
| Table of Contents |
|---|
| Tip | ||
|---|---|---|
| ||
For accessing your LDAP service over SSL, see Configuring Secure LDAP (LDAPS). |
Users and Groups
Users
| Info | ||
|---|---|---|
| ||
When using the LDAP Authenticator, credentials are authenticated at the time of login directly against the remote service. In order for Datameer X to manage authorization and object permissions, a Datameer X user entity is required to represent the remote user. It useful to think of users being imported into Datameer X from LDAP with the remote server always ensuring that users have valid, active credentials. When a user is imported into Datameer X, a user entity is created using the remote unique identifier as the Datameer X username and populated with other account details, i.e. the email address. |
| Info | ||
|---|---|---|
| ||
If authenticating with Active Directory or LDAP, users executing jobs must be listed in the authenticator. For added security, executing jobs as a users not present in the authenticator is not possible. |
Groups
| Info | ||
|---|---|---|
| ||
During import, Datameer X creates groups, based on the groups contained in the LDAP directory. This allows the use of existing LDAP groups for Datameer X access control as the group memberships are mirrored across systems. The users' group memberships and user details are updated on every login to ensure that any changes to authorization policies in LDAP are reflected in every Datameer X session. Since we rely on LDAP groups when the LDAP Authenticator is in use, there is no facility to create groups within Datameer. Datameer X can handle at maximum 500 LDAP groups. |
| Info | ||||
|---|---|---|---|---|
| ||||
Many times an all lowercase username is required for proper Unix group authentication. Instead of needing to change all user names to lowercase characters, Datameer X has the following property file to transform a username into all lowercase before passing it to the hadoop client API(s) to account for this issue:
To enable this feature, add the above property file to the custom Hadoop properties. |
Preparing the Authentication
| Info | |||||
|---|---|---|---|---|---|
| |||||
Make sure you have the superuser mode enabled in the 'live.properties' and have the password handy when configuring the authentication. For that, check if the deployment property 'das.superuser.enabled' is true and have the values for 'das.superuser.username' and 'das.superuser.password' handy. NOTE: If you are using a custom deploy mode via 'DAS_DEPLOY_MODE' then use the properties file for that mode, live.properties is the default).
|
Configuring an Active Directory and LDAP Authentication
To configure Datameer X to use your LDAP or Active Directory service:
- Click on the "Admin" tab and select "Authentication". The page 'Authentication' opens.
- Click "Edit". The authentication configuration page opens.
- Select "Remote Authentication System", select "ActiveDirectory/ LDAP" from the drop-down and click "Next".
- Enter the username and password for the default user.
- Enter the server URL.
INFO: The URL should have the form of 'ldap://server:port'. The port numbers are: LDAP/S - 389/636 or Active Directory - 3268.
- If needed, select "Use default user" if the server connection should use the default user to connect.
- If needed, enter the username and password.
- Enter the search base query.
- Enter the user definition query.
- If needed, enter the group definition query.
- If needed, define the pagination control.
- If you want to add multiple LDAP server, click "Add server connection". Another 'Server Connection' section opens and can be configured and deleted if non needed furthermore.
- Enter the username attribute that defines a username and must be unique across all users.
- Enter the email attribute.
- If needed, enter the attributes for impersonation and/ or salt.
- Enter the attribute for group names.
- If needed, enter further group related attributes as well as group relates fields, e.g. 'Virtual Group'.
INFO: The checkbox 'Mixed mode' is enabled by default and enables both internal user management as well as SAML. Having this disabled, the internal user management is disabled.
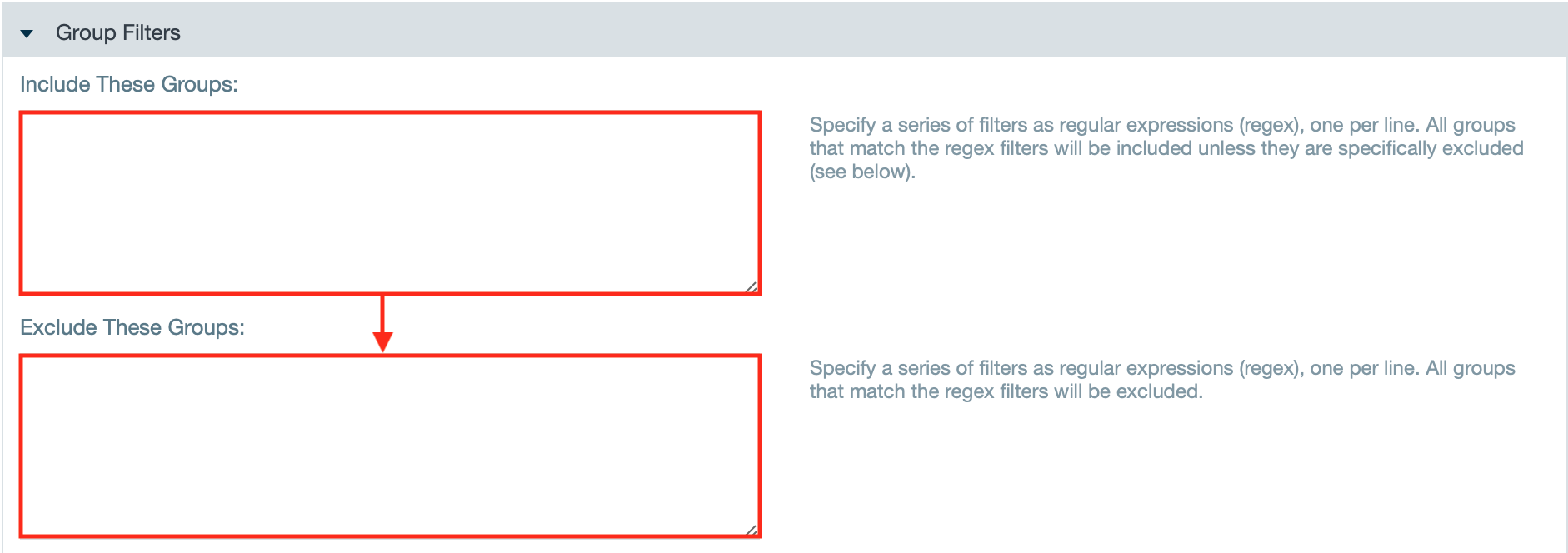
- If needed, enter group filters to include or exclude groups with regex.
- If needed, check the checkbox "Ignore Case" to perform a case sensitive match when filtering group names.
- Confirm the configuration with "Save". Configuring Datameer X to use LDAP or Active Directory authentication is finished.
Importing Users/Groups
Once you have successfully configured your LDAP connection, you can now import users into Datameer X enabling users to access the system. Because AD/LDAP is active, Datameer's internal authentication method is disabled. Therefore, admins must create all groups needed in the AD and add the users there before importing them. To import, click Users from the Admin menu.
...
Highlight multiple users/groups to to perform bulk role updates or deletions. It is also possible to bulk import users from your LDAP authenticator.
| Info | ||
|---|---|---|
| ||
The username and email address aren't editable as they are provided bythe LDAP service. Only Enable/Disable, Roles, and comments are editable from this screen. |
...
In the Query Options section of the Authenticator configuration screen, you can define a search base that limits the scope of the LDAP query. For example, if we have a search base for a Datameer X LDAP server DC=datameer,DC=local and it contains 3,000 users which is over the limit of 1,000 results, we can refine it to include only the organizational unit we want, OU=BarUnit,DC=Datameer X DC=local which contains only 1,000 users.
Now we can successfully import users from the organizational unit BarUnit and below in the LDAP tree.
...
The Query Options section also contains a field for configuring a User Filter. This is analogous to an SQL WHERE clause used when Datameer X queries for LDAP users. You can filter any attribute associated with a user in your LDAP server. As an example, we could filter users based on their membership in either the 'Finance' or 'IT' department. This would make only users matching the filter available for import into Datameer. The filter is defined using normal LDAP query syntax:
| Info | ||
|---|---|---|
| ||
The above query says, "Find objects which are of objectClass 'person' and have a department value of either 'Finance' or 'IT'". For more details about LDAP query syntax, go here. |
...